Network Mapping
Description
Info
Level: Beginner
Presenter: Eli the Computer Guy
Date Created: November 9, 2010
Length of Class: 51 Minutes
Tracks
Networking
Hacking
Computer Security /Integrity
Prerequisites
Introduction to Networking
Purpose of Class
This class teaches students how to map a local network.
Chapters
Introduction (00:00)
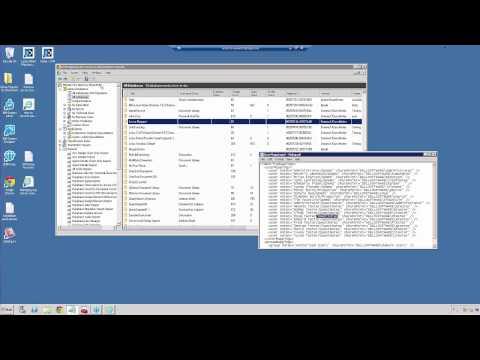
How Network Mapping Works (03:12)
DOS Tools (11:44)
Network Mapping Software (34:54)
Security Considerations (44:14)
Final Thoughts (48:21)
Class Notes
How it Works
ICMP -- Internet Control Message Protocol -- part of Internet Protocol
Echo request
Used by OS's to send error messages
Ports Scanning
All network applications require specific ports to be open
SMB Shares
Server Message Block is used for Windows File and Print Sharing
SNMP
Simple Network Management Protocol
Part of IP
Allows communication of alerts for numerous types of problems on a system from applications, the operating systems or even the hardware
Uses Agents,Traps and Network Management System
Agents are pieces of software installed on the monitored systems
Traps are alerts that are set for the Agent (CPU goes over 90% for 5 minutes)
Network Management System receives alert messages from Traps.
SNMP Service must be running
Uses UDP Ports 161, 162
Basic DOS Commands
IPCONFIG
Ipconfig /all -- Shows current IP information fro system
Ipconfig /release -- Releases DHCP IP Address
Ipconfig /renew - Acquires a new IP Address from DHCP Server
Ping
i. IP Protocol
Ping 10.1.10.1 -- Pings either an IP Address or a Domain Name
Ping /? -- Shows arguments fro Ping command
Ping 10.1.10.1 --n 6 -- -n argument changes the number of pings sent
Ping xxx --i 200 -- -i argument changes the Time To Live for a Ping
Tracert
IP Protocol
tracert www.everymanit.com -- Shows all of the routers on the path to the destination
Network Mapping Software Description
Network Mapping Software Discovers Devises and Systems on Your Network
Can be free or very expensive
There are numerous types of software that find different information
Security Security Good vs. Bad
Turn off SNMP services? -- SNMP can be very useful if you use it.
Use firewalls -- Firewalls can block Network Mapping Software from discovering devices on the network
Turn off Ping Echo -- You can turn off Ping Echo using security software. Ping is a very useful diagnostic tool, and can cause confusion for technicians if standard systems cannot be pinged.
Final Thoughts
Network Mapping can be used for Good and Bad purposes. You must weigh utility vs. security when deciding to allow or block the ability to map a netwrk.
Resources
Spiceworks
PortScan