Recently added videos
-
00:38 Popular

Get Schooled On The Biggest Battle In Data Center History
Added 342 Views / 0 LikesYou see a data center. But for some, it's a battleground. An eternal face off between physical and virtual, software and hardware, scalability and performance. There's only one way to resolve this. And it might not be what you expect. Get the lowdown from
Featured -
00:34 Popular

Do You Have Enough Mojo To Win The Data Center Rap Battle?
Added 409 Views / 0 LikesKathleen is just trying to get apps out the door. But the hardware guys keep getting in the way. She's ready for battle, a rap battle. Or so she thinks. Good thing corporate sent a rap coach to help out.
Featured -
10:54 Popular

Enhance Content Sharing Experience With Juniper Content Encore Over Contrail
Added 530 Views / 0 LikesThis video showcases Contrail as a powerful platform to enable elastic deployment of Content Delivery Network services to significantly enhance the user experience of secure internal content sharing and video streaming within your VPN.
Featured -
01:27 Popular

Juniper Networks And The IBM Accelerated Discovery Lab
Added 328 Views / 0 LikesWil Plouffe, Infrastructure Architect at the IBM Accelerated Discovery Lab, describes the critical role that Juniper's QFabric, security and management technologies play in this collaborative effort to explore big data.
Featured -
01:34 Popular

Juniper Networks And VMware: Integrating Physical And Virtual Worlds
Added 516 Views / 0 LikesStephen Mullaney, SVP and General Manager or VMware's Networking and Security Business Unit, describes the challenges of integrating physical and virtual worlds, and how Juniper and VMware are working together to deliver innovative solutions that address
Featured -
10:04 Popular
Elastic SSL VPN Service Over Contrail For Secure Mobile Connectivity
Added 417 Views / 0 LikesThis video showcases Contrail as a powerful platform to enable elastic and agile deployment of SSL VPN service to significantly facilitate secure mobile connections to enterprise critical resources and applications to accommodate the increasingly mobile a
Featured -
05:28 Popular

The Security Whiteboard
Added 409 Views / 0 LikesThis is an introduction to an ongoing series to discuss the latest updates in security. This episode focuses on Next-Gen Firewalls -- where they are today, how we got here, and what comes next.
Featured -
05:41 Popular
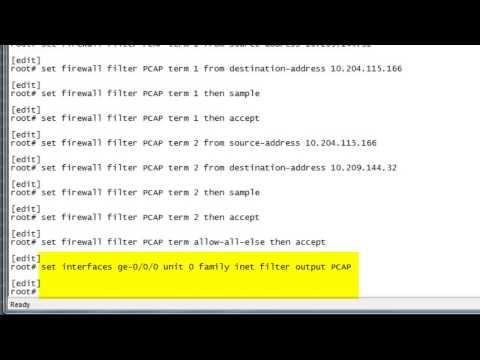
SRX/J Series: How To Create PCAP Packet Capture: Juniper KBTV
Added 714 Views / 0 LikesThis video provides a demonstration on how to create a PCAP packet capture on Juniper SRX and J Series devices. The text version of this video is available at http://kb.juniper.net/kb11709.
Featured -
01:41 Popular

What It Means To Be A Juniper Ambassador
Added 315 Views / 0 LikesMembers of the Juniper Networks Ambassador Team tell us what it means to them to be part of the program. This video highlights the following team members: Kevin Barker Martin Brown Steve Puluka Ben Dale David Roy Scott Ware
Featured -
05:33 Popular

WLAN - WLC Troubleshooting
Added 369 Views / 0 LikesThe WLAN - show tcp Learning byte discusses the show tcp command in the MSS OS, and explains the purpose of this command as an aid to troubleshooting connectivity towards a Wireless LAN Controller. This Learning Byte includes a demonstration of the show t
Featured -
10:34 Popular
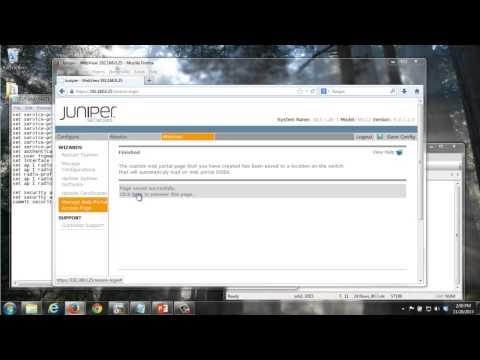
WLAN - Configuring A WLAN Captive Portal
Added 426 Views / 0 LikesThe Configuring a WLAN Captive Portal shows how to configure a captive portal for user login to a wireless network. It demonstrates how to set this up through both the Ringmaster GUI and the WLC CLI. Presenter: Kevin Barker, Juniper Ambassador, JNCI Relev
Featured -
10:46 Popular

CTP Password Recovery
Added 359 Views / 0 LikesThe CTP password recovery Learning Byte provides the steps required to recover from an unknown root password. This Learning Byte is appropriate for all users of the Juniper CTP solution. Presenter: Gerben Camp, Instructor Relevant to OS Releases: CTPOS 6.
Featured -
14:17 Popular
Junos Space Service Now
Added 431 Views / 0 LikesThe Junos Space Service Now Learning Byte explores the enablement and configuration of the Junos Space Service Now and Service Insight applications. After viewing this Learning Byte, you will understand how to connect to Juniper Support Systems (JSS) so y
Featured -
11:22 Popular
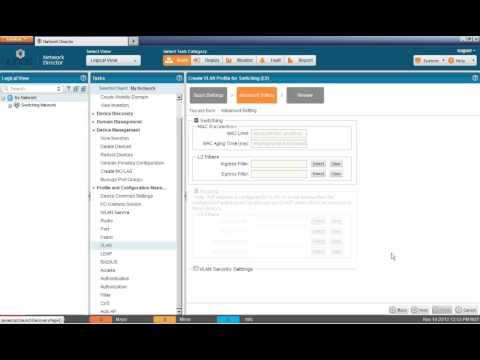
Building And Deploying VLAN Profiles In Network Director
Added 372 Views / 0 LikesThe Building and Deploying VLAN Profiles in Network Director Learning Byte covers how to build and deploy VLAN profiles in the Junos Space Network Director application. This byte is most appropriate for users who are new to working with Network Director o
Featured -
01:02 Popular

Data Center Rap Battle: Training References
Added 486 Views / 0 LikesYou can't just flip through a magazine or switch on the news, you've got to dig deep for inspiration if you want winning rhymes. As any rap coach will tell you, to fully master this craft you've got to know facts, figures and culture like a boss. Do any o
Featured -
02:04 Popular

What's Really Going Down In The Data Center
Added 284 Views / 0 LikesThe data center, based on physical boxes, has been around since the 1960s. Today, it's the epicenter of all business. To keep data safe, it was kept on premises. But as needs scaled, so did the number of boxes...and complexity. Enter virtualization, bring
-
00:21 Popular

SA/MAG Series: How To Identify The OS Type Of Remote Access Users
Added 479 Views / 0 LikesThis video demonstrates how to use Host Checker to identify and log the OS type of remote access users in the User Access Log.
Featured -
02:50 Popular

Employee Collaboration
Added 498 Views / 0 LikesLutz Klaus, Snr Director of Enterprise Marketing, EMEA at Juniper Networks discusses optimizing the network environment to support Microsoft Lync to create an Empowered Enterprise. For further information please visit http://www.juniper.net/uk/en/empowere
Featured -
04:14 Popular

Connecting CSE2000 To PTX5000 Router
Added 306 Views / 0 LikesThis video shows how to connect a CSE2000 device to a PTX5000 Router. The written form of this video can be read at http://www.juniper.net/documentation/en_US/release-independent/cse-series/topics/task/operational/cse2000-connecting-router.html
Featured -
09:22 Popular
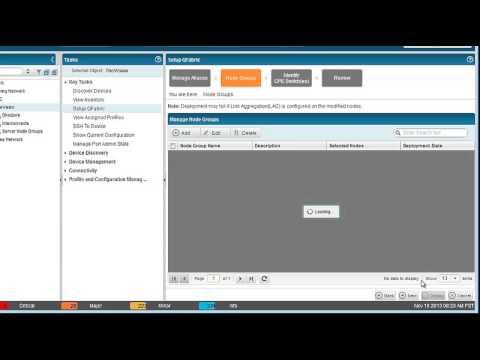
Network Director 1.5 QFabric Features
Added 435 Views / 0 LikesThis video describes and demonstrates the QFabric management, analysis, and monitoring features in Juniper Networks Junos Space Network Director 1.5. The written form of this video can be read at http://www.juniper.net/documentation/en_US/network-director
Featured -
02:28 Popular

Juniper Innovation Delivers Expanded SDN Portfolio
Added 426 Views / 0 LikesJuniper Networks' EVP, Rami Rahim discusses why service providers must create an agile infrastructure that's simple to manage, efficient and programmable, and how Juniper can provide them with a service creation platform that empowers end users and delive
Featured -
03:12 Popular

Deception Force: Official Launch Trailer
Added 387 Views / 0 LikesIt started with an ad for an IT security professional. But it quickly took another turn in this pulse-pounding trailer for the exciting new mobile game from Juniper Networks. Learn the secrets behind Deception Force, an elite team of data center security
Featured -
03:40 Popular

Replacing A PIC In A PTX3000 Router
Added 348 Views / 0 LikesThis video describes removing and installing a PIC in a PTX3000 router. The written form of this video can be read at http://www.juniper.net/documentation/en_US/release-independent/junos/topics/task/installation/pic-ptx3000-replacing-multi-task.html
Featured -
18:16 Popular
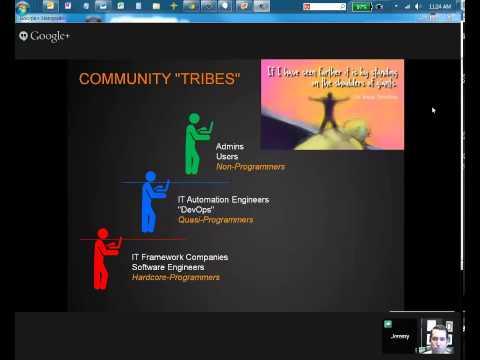
Programming For Non-programmers
Added 436 Views / 0 LikesHow to migrate from traditional networking into the world of network automation without being a hardcore programmer. "DevOps for Networking?": http://puppetlabs.com/blog/devops-networking Tech Wiki: http://techwiki.juniper.net/Automation_Scripting/Junos_O
Featured -
03:56 Popular

Data Center Security
Added 575 Views / 0 LikesIs there a difference between next gen firewalls and data center security? Yes! This animation describes Juniper's unique data center security solutions, and how they compare with next gen firewalls.
Featured -
05:19 Popular
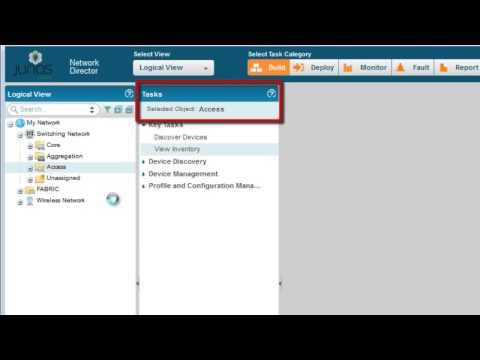
Introduction To The Network Director 1.5 User Interface
Added 490 Views / 0 LikesThis video provides an introduction to the Juniper Networks Junos Space Network Director 1.5 User Interface. It describes and demonstrates the user interface's main functional areas and typical workflow. The written form of this video can be read at http:
Featured -
22:23 Popular

The Next World War Will Be Fought In Silicon Valley
Added 455 Views / 0 LikesWe are under attack, and we are not allowed to fight back. Everyone has a breaking point. What's yours? Nawaf Bitar Senior Vice President and General Manager, Security Business Unit, Juniper Networks, Inc. This is the 2014 RSA keynote. It is a POV from Na
Featured -
59:30 Popular

Juniper Networks Certification Webcast - March 2014
Added 576 Views / 0 LikesThis 50-minute webcast features Shaygan Kheradpir, CEO of Juniper Networks. In this up close and personal session with Shaygan, he shares how his 27 years in the networking "trenches" and experience as a Juniper customer shape his understanding of the net
Featured -
02:11 Popular
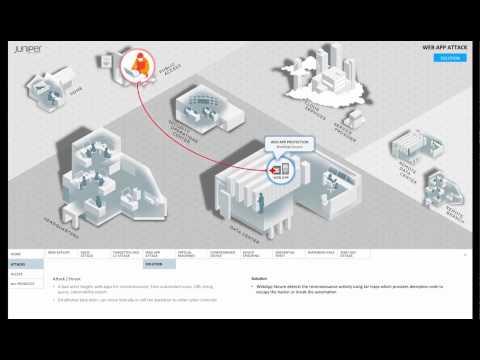
Web App Attack
Added 353 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
03:34 Popular
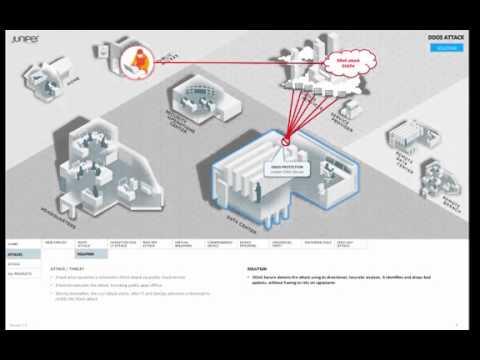
DDoS Attack
Added 438 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
01:55 Popular

New Exploit
Added 265 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
14:50 Popular
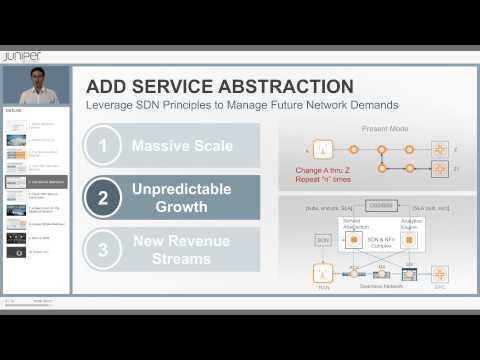
Mobile Backhaul Solution
Added 535 Views / 0 LikesDavid Noguer Bau describes the mobile network operator environment as the perfect storm: the smart network meets the smart device. He talks about the challenges faced by operators in their backhaul networks and positions Junipers solutions in this context
Featured -
18:13 Popular
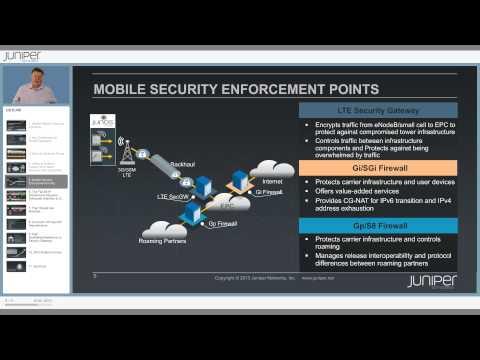
Mobile Network Security Solutions
Added 515 Views / 0 LikesThe mobile experience is now at the front line of brand management of which security is a huge part. This video highlights some of the challenges for mobile operators and proposes some solutions. It takes the form of a 20 minute presentation delivered by
Featured -
01:52 Popular

Juniper Networks ON Enterprise
Added 412 Views / 0 LikesThis short animated demo provides an overview of Juniper Networks always-ON Enterprise wired and wireless solution for the campus.
Featured -
05:00 Popular
EX Series: How To Create A Link Aggregation Group (LAG) - Juniper KBTV
Added 456 Views / 0 LikesThis video demonstrates the steps necessary to create a Link Aggregation Group or LAG on an EX Series device. The text version is available at https://kb.juniper.net/kb10927
Featured -
01:33 Popular

UK Introduction To RAND Cybercrime Research, Sponsored By Juniper.
Added 428 Views / 0 LikesMark Quartermaine, Area Vice President of UK & Ireland, Juniper Networks discusses the key findings of the Juniper Networks sponsored RAND Cybercrime Research report - "Markets for Cybercrime Tools and Stolen Data: Hackers' Bazaar"
Featured -
10:01 Popular
Juniper On Juniper WAN Project
Added 443 Views / 0 LikesThis video is a summary of the new WAN architecture implemented internally at Juniper. The new architecture allows enterprises to have greater control over their network using Juniper products.
Featured -
02:21 Popular
Credential Theft
Added 315 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
13:14 Popular
OSPFv2 Adjacency Formation
Added 378 Views / 0 LikesThe OSPFv2 Adjacency Formation Learning Byte explains the fundamentals of how OSPF adjacencies are formed, in particular on devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriate for new users, or anyone l
Featured -
12:09 Popular
Junos Space: Policy Versioning In Security Director
Added 424 Views / 0 LikesThe Junos Space: Policy Versioning in Security Director Learning Byte covers how to work with policy snapshots in the Security Director application. This byte is most appropriate for users who have intermediate experience working with Security Director or
Featured -
11:46 Popular
Junos Space Network Director Image Management
Added 470 Views / 0 LikesThe Junos Space Network Director Image Management Learning Byte covers how to stage and upgrade Junos devices in the Junos Space Network Director application. This byte is most appropriate for users who are new to working with Network Director or anyone l
Featured -
13:49 Popular

Configuring Route-Based Site-to-Site IPSec VPN On The SRX
Added 617 Views / 0 LikesThe Configuring Route-Based Site-to-Site IPsec VPN on the SRX Series Learning Byte discusses the configuration of a secure VPN tunnel between two Juniper Networks SRX-series devices. The concept of route-based VPN is briefly discussed and the commands nee
Featured -
12:57 Popular
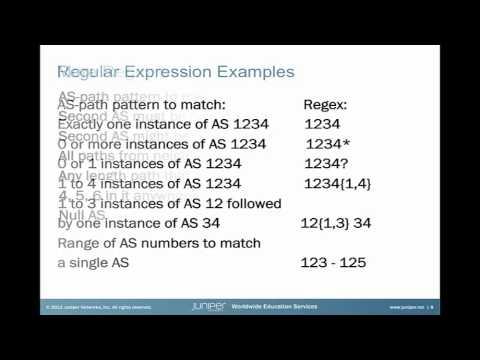
AS-Path Regular Expressions
Added 464 Views / 0 LikesThe AS-Path Regular Expressions Learning Byte demonstrates configuration examples of AS-Path regular expressions, which are pattern matching variables that can be referenced in a routing policy. Presenter: David Williams, Technical Instructor Relevance to
Featured -
02:46 Popular

Juniper Security Ecosystem Introduction
Added 621 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
03:48 Popular

Access
Added 444 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
00:47 Popular
Zero Day
Added 297 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
02:01 Popular
Device Spoofing
Added 309 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
01:49 Popular
Compromised Device
Added 289 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
02:53 Popular

Virtual Machine Security
Added 477 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
11:59 Popular
OSPFv2 Authentication
Added 408 Views / 0 LikesThe OSPFv2 Authentication Learning Byte explains the options and functionality of OSPFv2 authentication for devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriate for new users, or anyone looking to enable
Featured -
08:41 Popular
Basic OSPFv2 Configuration
Added 507 Views / 0 LikesThe Basic OSPFv2 Configuration Learning Byte explains the initial steps to enable OSPFv2 on devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriate for new users, or anyone looking to learn about enabling O
Featured -
16:05 Popular

QFabric Solution Revenue Port Layout
Added 327 Views / 0 LikesThe QFabric Solution Revenue Port Layout Learning Byte briefly describes the supported interface types and speeds on the QFX3600 switch and shows you how to configure them, both in standalone and Fabric mode. Presenter: Gerben Camp, Technical Instructor R
Featured -
06:21 Popular
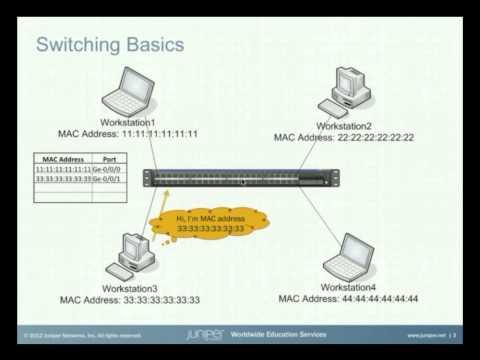
Switching Basics On The EX Series Switches
Added 633 Views / 0 LikesThe Switching Basics on EX Series Switches Learning Byte covers the basics of switching and how frames are sent between hosts on the network and how the switch knows where to send the frame. This Learning Byte is appropriate for anyone looking to learn th
Featured -
01:46 Popular

How Do You Preserve Lossless Behavior On An SDN Or Overlay Network?
Added 319 Views / 0 LikesBrief overview of how to use Priority-based Flow Control (PFC) to preserve lossless transport of storage traffic across a converged data center network. The written form of this video can be read at http://www.juniper.net/documentation/en_US/junos13.2/top
Featured



