Juniper Networks
We believe the network is the single greatest vehicle for knowledge, collaboration, and human advancement that the world has ever known. Now more than ever, the world relies on high-performance networks. And now more than ever, the world needs network innovation to unleash our full potential.
Every day, Juniper Networks is helping our customers build the best networks on the planet. Every innovation we envision, every technology we create is informed by our desire to help solve our customers’ toughest challenges so they can compete and thrive today and into the future.
For more information, visit our website www.juniper.net
-
59:30 Popular

Juniper Networks Certification Webcast - March 2014
Added 458 Views / 0 LikesThis 50-minute webcast features Shaygan Kheradpir, CEO of Juniper Networks. In this up close and personal session with Shaygan, he shares how his 27 years in the networking "trenches" and experience as a Juniper customer shape his understanding of the net
Featured -
10:01 Popular
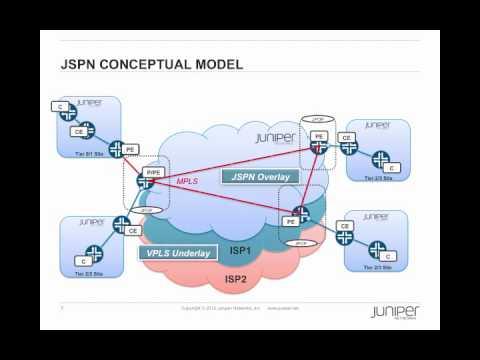
Juniper On Juniper WAN Project
Added 333 Views / 0 LikesThis video is a summary of the new WAN architecture implemented internally at Juniper. The new architecture allows enterprises to have greater control over their network using Juniper products.
Featured -
01:33 Popular

UK Introduction To RAND Cybercrime Research, Sponsored By Juniper.
Added 318 Views / 0 LikesMark Quartermaine, Area Vice President of UK & Ireland, Juniper Networks discusses the key findings of the Juniper Networks sponsored RAND Cybercrime Research report - "Markets for Cybercrime Tools and Stolen Data: Hackers' Bazaar"
Featured -
05:00 Popular
EX Series: How To Create A Link Aggregation Group (LAG) - Juniper KBTV
Added 355 Views / 0 LikesThis video demonstrates the steps necessary to create a Link Aggregation Group or LAG on an EX Series device. The text version is available at https://kb.juniper.net/kb10927
Featured -
01:52 Popular

Juniper Networks ON Enterprise
Added 293 Views / 0 LikesThis short animated demo provides an overview of Juniper Networks always-ON Enterprise wired and wireless solution for the campus.
-
18:13 Popular
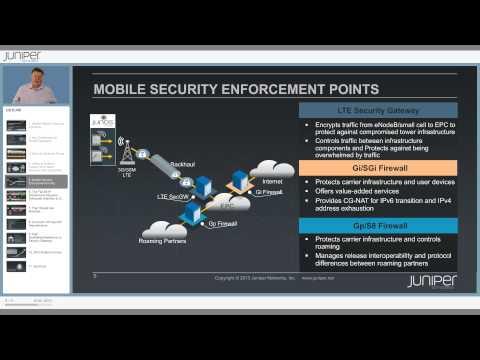
Mobile Network Security Solutions
Added 395 Views / 0 LikesThe mobile experience is now at the front line of brand management of which security is a huge part. This video highlights some of the challenges for mobile operators and proposes some solutions. It takes the form of a 20 minute presentation delivered by
Featured -
14:50 Popular
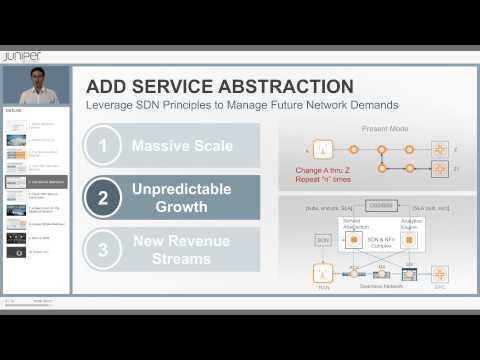
Mobile Backhaul Solution
Added 410 Views / 0 LikesDavid Noguer Bau describes the mobile network operator environment as the perfect storm: the smart network meets the smart device. He talks about the challenges faced by operators in their backhaul networks and positions Junipers solutions in this context
Featured -
01:55 Popular

New Exploit
Added 183 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
03:34 Popular
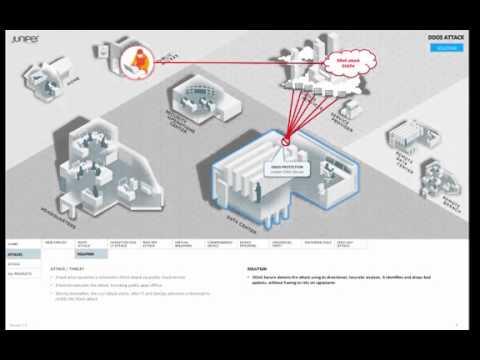
DDoS Attack
Added 321 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
02:11 Popular
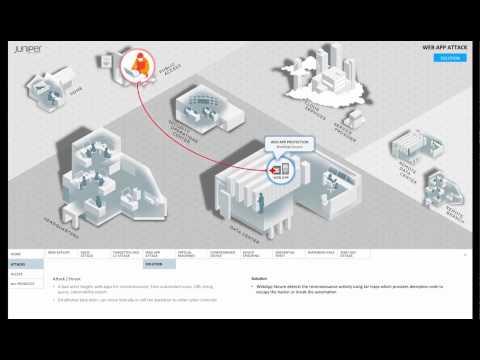
Web App Attack
Added 256 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
02:53 Popular

Virtual Machine Security
Added 382 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
01:49 Popular
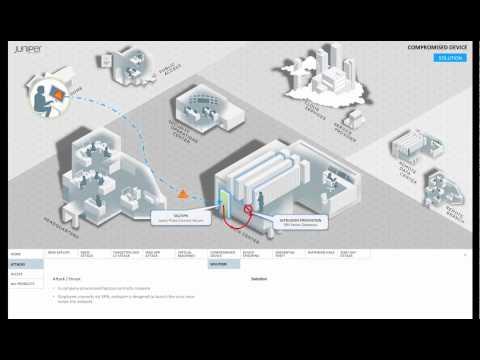
Compromised Device
Added 214 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
02:21 Popular
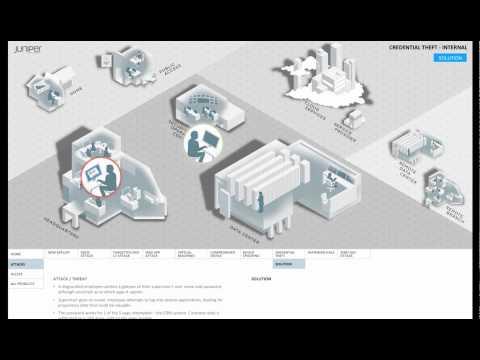
Credential Theft
Added 240 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
02:01 Popular
Device Spoofing
Added 230 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
00:47 Popular
Zero Day
Added 209 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
-
03:48 Popular

Access
Added 333 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
02:46 Popular

Juniper Security Ecosystem Introduction
Added 502 Views / 0 LikesThis video series describes different threat, attack, and secure access scenarios, and suggests ways that Juniper security technology can solve them.
Featured -
12:57 Popular
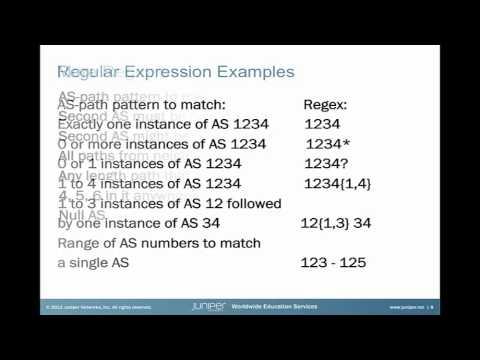
AS-Path Regular Expressions
Added 360 Views / 0 LikesThe AS-Path Regular Expressions Learning Byte demonstrates configuration examples of AS-Path regular expressions, which are pattern matching variables that can be referenced in a routing policy. Presenter: David Williams, Technical Instructor Relevance to
Featured -
13:49 Popular

Configuring Route-Based Site-to-Site IPSec VPN On The SRX
Added 509 Views / 0 LikesThe Configuring Route-Based Site-to-Site IPsec VPN on the SRX Series Learning Byte discusses the configuration of a secure VPN tunnel between two Juniper Networks SRX-series devices. The concept of route-based VPN is briefly discussed and the commands nee
Featured -
11:46 Popular
Junos Space Network Director Image Management
Added 359 Views / 0 LikesThe Junos Space Network Director Image Management Learning Byte covers how to stage and upgrade Junos devices in the Junos Space Network Director application. This byte is most appropriate for users who are new to working with Network Director or anyone l
Featured




