Juniper Networks
We believe the network is the single greatest vehicle for knowledge, collaboration, and human advancement that the world has ever known. Now more than ever, the world relies on high-performance networks. And now more than ever, the world needs network innovation to unleash our full potential.
Every day, Juniper Networks is helping our customers build the best networks on the planet. Every innovation we envision, every technology we create is informed by our desire to help solve our customers’ toughest challenges so they can compete and thrive today and into the future.
For more information, visit our website www.juniper.net
-
13:14 Popular
OSPFv2 Adjacency Formation
Added 272 Views / 0 LikesThe OSPFv2 Adjacency Formation Learning Byte explains the fundamentals of how OSPF adjacencies are formed, in particular on devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriate for new users, or anyone l
-
11:59 Popular
OSPFv2 Authentication
Added 296 Views / 0 LikesThe OSPFv2 Authentication Learning Byte explains the options and functionality of OSPFv2 authentication for devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriate for new users, or anyone looking to enable
-
09:36 Popular
OSPFv2 Neighbor Adjacency/Timers
Added 285 Views / 0 LikesThe OSPFv2 Neighbor Adjacency/Timers Learning Byte explains the fundamentals of how hello and dead timers work between OSPF neighbors, in particular on devices running the Junos OS. With a short lecture followed by a demonstration, this Byte is appropriat
-
01:51 Popular

Outsourcery: Building A Secure New Platform For Enterprise And Government Customers
Added 366 Views / 0 LikesOutsourcery Builds a Secure New Platform for Enterprise and Government Customers
Featured -
13:40 Popular
Overcoming Overlapping IP Addresses With Static NAT
Added 405 Views / 0 LikesThe Overcoming Overlapping IP Addresses with Static NAT Learning Byte covers how to configure static NAT on SRX Series devices to overcome problems with overlapping IP addresses. This byte is most appropriate for users who are looking to understand how to
Featured -
10:37 Popular
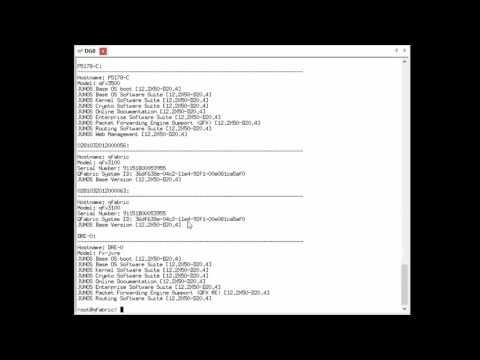
Overview And Upgrade Of A QFabric System
Added 320 Views / 0 LikesThe Overview and Upgrade of a QFabric System learning byte provides a brief overview of the basic components used in a QFX3000-G and QFX3000-M QFabric system. It also covers the necessary steps when upgrading the QFabric system. A hands on example upgradi
Featured -
02:00 Popular

Overview Of Juniper Software Advantage (JSA) For Security
Added 347 Views / 0 LikesQuickly provides background of why Juniper Software Advantage, a new software licensing model, is beneficial for customers of Juniper security products.
Featured -
03:36 Popular

Paralympic Champion Stephen Lawler
Added 408 Views / 0 LikesParalympic Skier Stephen Lawler tells his story in the context of what he has overcome, his goals and how he is perceived as an role model. He thanks Juniper Networks for sponsoring him.
Featured -
03:43 Popular

Partners For The Networking Lifecycle
Added 297 Views / 0 LikesNetworking projects require specialized skills, and different ones for each phase of the Networking Lifecycle – Plan, Build, and Operate. Joe Robertson says that often you will get the best results from network integrators. Vendor certification of the int
-
02:18 Popular

Paul Gainham Discusses Consumerisation Of IT Driving The Empowered Enterprise
Added 245 Views / 0 LikesTwo decades ago, the personal computer revolutionised how offices worked: it put the creation of data, and access to it, in our hands. Companies who recognised this embraced the power of the PC and quickly drove competitive advantage for themselves. Today
-
03:39 Popular

Paul Gainham Video Blog 2013 Key IT Trends
Added 340 Views / 0 LikesPlotting a path through Hype, Religion and Reality - Three Trends to watch out for in 2013 As the Christmas lights go on and Christmas Carol's begin to fill the air, what better time to look forward to the year ahead and pick out a few key trends that may
Featured -
01:35 Popular
Peer1 Hosting Selects Juniper Networks
Added 250 Views / 0 LikesPeer1 Hosting selects Juniper Networks to power one of the most energy efficient data centers in the U.K.
-
16:33 Popular
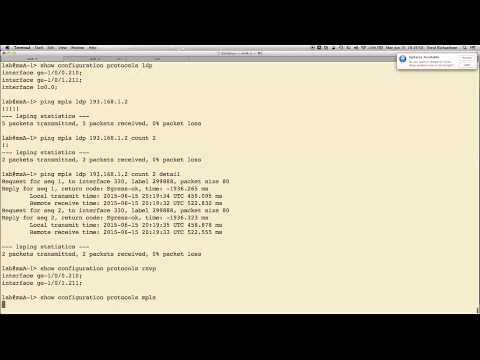
Ping MPLS For LSPs
Added 357 Views / 0 LikesThe Ping MPLS for LSPs learning byte provides detailed coverage of the operational mode ping command that is available for MPLS LSPs. It answers questions that are usually asked by attendees of the Junos MPLS and VPNs class, or by customers working on a c
Featured -
16:09 Popular
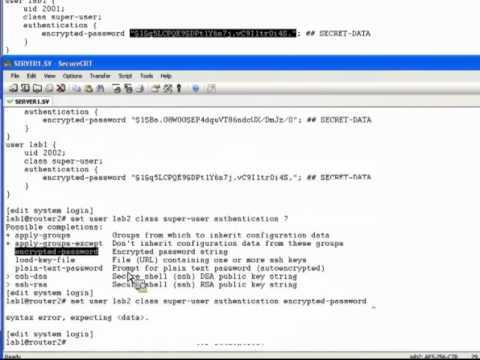
Plaintext-vs-Encrypted Passwords Learning Byte
Added 217 Views / 0 LikesThis Learning Byte is appropriate for new users of the Junos Operating System to assist them in understanding the differences between using plain-text and encrypted passwords when configuring login parameters. There is a short lecture followed by a demons
-
06:04 Popular

Planning For BYOD: Do Nothing. Do Something. Do The Right Thing.
Added 347 Views / 0 LikesPart 2 of our interview delves into the key findings of the report and discusses the solution side of BYOD - how to balance security and productivity, manage costs and move beyond the device to an integrated approach.
Featured -
14:16 Popular
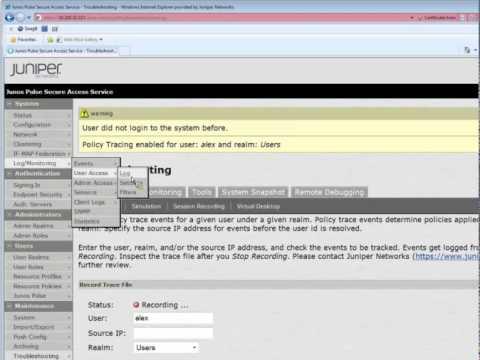
Policy Tracing Learning Byte
Added 318 Views / 0 LikesPolicy Tracing allows you to troubleshoot issues by tracking events when a user signs in and access resources using the Junos Pulse Secure Access Service. Policy Tracing is used simultaneously while a user is signing in and attempting to access secured re
Featured -
00:54 Popular

Power At The Edge Of The Network
Added 382 Views / 0 LikesLearn how to keep up with growing mobile data, broadband, video and metro traffic with the MX Series 3D Universal Edge Routers. Make your network more profitable with an edge that has the scalability and services to exceed rapidly growing routing needs.
Featured -
04:32 Popular

Pradeep Sindhu Honored In Washington
Added 305 Views / 0 LikesPradeep Sindhu, Vice Chairman, CTO and founder of Juniper, is sole recipient of the Morgan Stanley Leadership Award for Global Commerce, which recognizes "individuals whose personal leadership has made a critical contribution to the effective use of IT in
Featured






