Fortinet
Fortinet is a global leader and innovator in Network Security. Our mission is to deliver the most innovative, highest performing network security platform to secure and simplify your IT infrastructure. We are a provider of network security appliances and security subscription services for carriers, data centers, enterprises, distributed offices and MSSPs. Because of constant innovation of our custom ASICs, hardware systems, network software, management capabilities and security research, we have a large, rapidly growing and highly satisfied customer base, including the majority of the Fortune Global 100, and we continue to set the pace in the Network Security market. Our market position and solution effectiveness has been widely validated by industry analysts, independent testing labs, business organizations, and the media worldwide. Our broad product line of complementary solutions goes beyond Network Security to help secure the extended enterprise.
Fortinet is headquartered in Sunnyvale, California, with offices around the world. Founded in 2000 by Ken Xie, the visionary founder and former president and CEO of NetScreen, Fortinet is led by a strong and seasoned management team with deep experience in networking and security. For more information, visit our website at www.fortinet.com
-
03:41 Popular
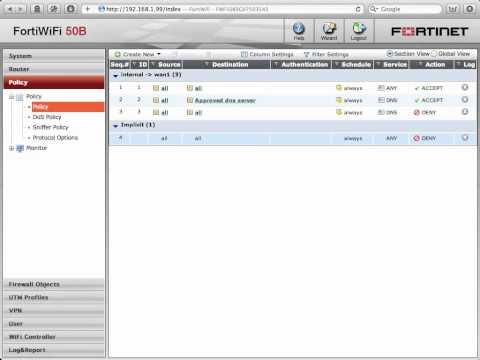
FortiGate Cookbook - Security Policies That Limit DNS Queries To Only One Approved DNS Server
Added 426 Views / 0 LikesCreate FortiGate security policies that block all DNS sessions except for sessions to the approved DNS server.
Featured -
02:36 Popular

FortiGate Cookbook - Packet Capture (5.2)
Added 514 Views / 0 LikesIn this video, you will learn how to use packet capture to monitor traffic passing through your FortiGate. Intercepting and capturing packets can be a useful troubleshooting tool, allowing you to analyze traffic in detail that has passed through your Fort
Featured -
02:22 Popular

FortiGate Cookbook - Client Reputation (5.0)
Added 275 Views / 0 LikesIn this video, you're going to learn how to enable and customize Client Reputation on your FortiGate unit. Client Reputation is a system unique to Fortinet products that automatically analyzes individual client data and scores clients by how much of a thr
-
02:44 Popular

FortiGate Cookbook - Blocking Google Accounts (5.2)
Added 316 Views / 0 LikesIn this video, you will learn how to block access to Google services such as Gmail for consumer accounts, while still allowing access for corporate accounts. If your organization has set up a Google corporate account to use Google service such as Gmail or
Featured -
04:01 Popular

FortiGate Cookbook - Web Filtering Quotas (5.2)
Added 308 Views / 0 LikesIn this video, you will learn to apply a web filter quota to an IPv4 policy with user or device authentication configured. You will set a 5 minute time limit, or quota, on visiting any websites in the General - Personal Interest category. This accommodate
Featured -
03:55 Popular

FortiGate Cookbook - IPsec VPN Remote Access For IOS (5.0)
Added 451 Views / 0 LikesCORRECTION 05/23/14: For this process to work, you will need to edit the VPN Phase 1 you create, and manually set the Mode to "Main (ID Protection)" rather than "Aggressive". Sorry for the confusion. In this video, you're going to learn how to set up a VP
Featured -
03:05 Popular

FortiGate Cookbook - DLP And File Filtering (5.0)
Added 319 Views / 0 LikesIn this video, you will learn how to prevent documents and files passing through your FortiGate firewall, using Data Leak Prevention and File Filtering. Visit Fortinet's documentation library at http://docs.fortinet.com or our video portal at http://video
Featured -
06:04 Popular

FortiGate Cookbook - Remote Browsing With VPN (5.2)
Added 350 Views / 0 LikesIn this video, you will learn how to use remote IPsec and SSL VPN tunnels to bypass internet access restrictions. A VPN tunnel is an encrypted traffic passage between two endpoints. In this example, the VPN tunnel is between a local user running FortiClie
Featured -
02:38 Popular

FortiGate Cookbook - Blocking HTTPS (5.0)
Added 265 Views / 0 LikesIn this video, you're going to learn how to block HTTPS traffic on your network with FortiGate Web Filtering. HTTPS allows secured access to various websites, and is now available on some social networking and media sites like Youtube and Facebook. Though
-
04:56 Popular

FortiGate Cookbook - Guest WiFi Accounts (5.2)
Added 282 Views / 0 LikesIn this video, you will learn how to set up guest WiFi access to a FortiAP in tunnel mode. You will set up a temporary guest WiFi user account that expires in 5 minutes and then create an optional admin account to manage guest accounts. Visit Fortinet's d
-
04:31 Popular

FortiGate Cookbook - Basic Web Filtering (5.0)
Added 375 Views / 0 LikesIn this video you're going to learn how to control which Internet websites users can access, by specifying web filtering profiles. Web filtering profiles let you identify and monitor all users accessing the Internet through your FortiGate unit by requirin
Featured -
05:26 Popular

FortiGate Cookbook - User/Device Scheduling (5.2)
Added 353 Views / 0 LikesIn this video, you will learn how to create schedules that restrict internet access based on time and user account info, allowing you more control over what content users can access and how much bandwidth is used. This example involves a full-time employe
Featured -
05:39 Popular
FortiGate Cookbook - WiFi And Wired Clients On The Same Subnet
Added 416 Views / 0 LikesYou want to put your WiFi users on the same network segment (or subnet) as your wired LAN users, but the FortiGate unit requires each network interface to have a single unique network segment. The solution is to create a software switch interface with the
Featured -
02:41 Popular

FortiGate Cookbook - Traffic Logging (5.2)
Added 368 Views / 0 LikesIn this example, you will enable logging to capture the details of the network traffic processed by your FortiGate unit. Capturing log details will provide you with detailed traffic information that you can use to asses any network issues. Visit Fortinet'
Featured -
03:40 Popular

FortiGate Cookbook - FSSO & Windows AD (5.0)
Added 258 Views / 0 LikesIn this video, you will learn how to integrate a FortiGate unit into a Windows Active Directory network to provide single-sign-on access to the Internet. Visit Fortinet's documentation library at http://docs.fortinet.com or our video portal at http://vide
-
03:22 Popular

FortiGate Cookbook - Scheduled BYOD Access (5.2)
Added 292 Views / 0 LikesIn this video, you will learn how to limit mobile device access to a wireless network by setting up a schedule. By using a schedule group and a BYOD device policy, you can limit mobile device internet usage outside of set hours. BYOD, or Bring Your Own De
-
07:59 Popular

FortiGate Cookbook – Self-Signed Certificates For SSL Inspection (5.2)
Added 293 Views / 0 LikesIn this video, you will learn how to prevent your users from getting security errors when you have full SSL inspection enabled. You will create a custom self-signed certificate with OpenSSL and then install it on your FortiGate. Unalike the FortiGate’s de
-
02:27 Popular
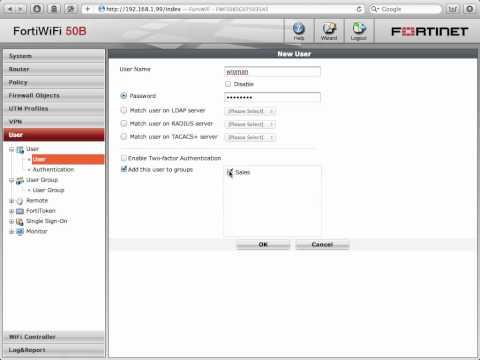
FortiGate Cookbook - Creating A Security Policy To Identify Users
Added 366 Views / 0 LikesEnable FortiGate user authentication by creating a user group named Sales and adding a user named wloman to this group. Then add an identity based policy to a security policy that accepts connections from the internal network to the Internet. Add the Sale
Featured -
04:08 Popular

FortiGate Cookbook - Transparent Mode (5.2)
Added 341 Views / 0 LikesIn this video, you will learn how to add a FortiGate in Transparent Mode to your existing network configuration, adding security with no added complexity. A FortiGate in Transparent Mode performs no routing or network address translation (NAT), but can st
Featured -
07:26 Popular

FortiGate Cookbook - Blocking Adult Content W/ SafeSearch (5.2)
Added 303 Views / 0 LikesIn this video, you will use FortiGate web filtering to apply SafeSearch to all Google results and also block access to websites in the adult/mature content FortiGuard category. In order to block encrypted traffic, you will also either use full SSL inspect
Featured




